[CyberLand News] Weekly #19 - Threats and Malware
Last news on threats, malware and vulnerabilties in the cyber land
Contents
Skype & Teams abuse via DarkGate malware
In recent findings, researchers have uncovered an ongoing cyber campaign that capitalizes on the popularity of messaging platforms, specifically Skype and Teams, to disseminate the malicious DarkGate malware. Over a three-month span, from July to September, Trend Micro diligently monitored this campaign's devious activity as it utilized instant messaging services to deliver a VBA loader script to unsuspecting victims.
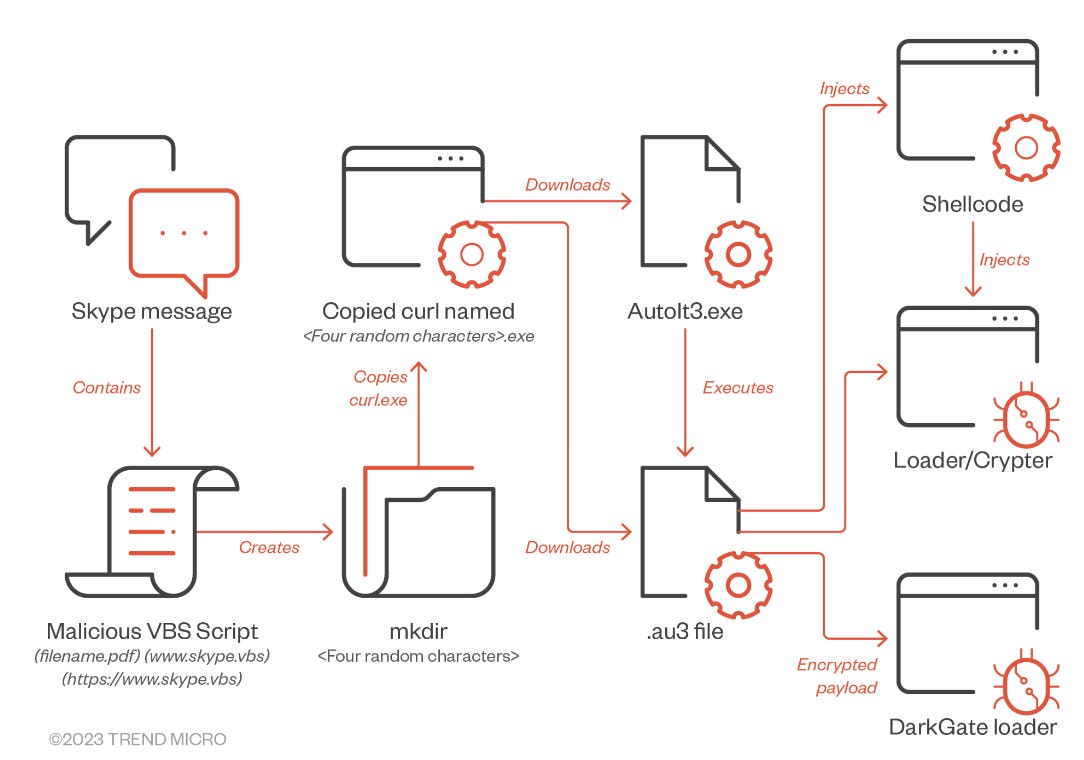
The perpetrators behind this campaign demonstrated an adept use of widely-used messaging platforms like Skype and Teams as conduits for delivering a script that acted as a loader for a powerful second-stage payload. Concealed within an AutoIT script, this secondary payload harbored the notorious DarkGate malware, known for its versatility and potency. Researchers suspect that threat actors gained access to the accounts within these messaging applications through the opportunistic exploitation of leaked credentials available on cybercrime forums.
DarkGate, a malware first identified by Fortinet researchers in 2017, possesses multifaceted capabilities, including executing discovery commands, autonomous updates, remote access software implementation (such as RDP, hVNC, and AnyDesk), cryptocurrency mining, keylogging, browser data extraction, and privilege escalation.
In the latest campaign, threat actors manipulated the trust between two organizations, deceiving recipients into executing a VBA script. Once they accessed the victim's Skype account, the attackers would hijack an existing messaging thread and cleverly name files to match the chat's context. Messages sent to victims contained a VBS script, its filename carefully crafted to appear as a legitimate PDF document, lulling users into a false sense of security.
Trend Micro's warning underscores the need for careful scrutiny when introducing new applications into an organization, as they can substantially expand the attack surface. The report concludes that cybercriminals can leverage these payloads to infiltrate systems with various malware types, including info stealers, ransomware, malicious remote management tools, and cryptocurrency miners. The campaign's success highlights the necessity for robust cybersecurity measures and vigilant monitoring of instant messaging apps to counter such threats.
More details in “DarkGate Opens Organizations for Attack via Skype, Teams“
Additional info in “DarkGate Malware Activity Spikes as Developer Rents Out Malware to Affiliates“
The new Magecart web skimming campaign
A recently unveiled, highly sophisticated Magecart web skimming campaign has been systematically targeting Magento and WooCommerce websites. A number of victims affected by this campaign are linked to prominent organizations operating in the food and retail sectors.
The campaign has been active for a few weeks, with some cases extending even longer. Notably, it has impressed security experts with an advanced concealment technique that had not been previously encountered.
Typically, Magecart attacks begin by exploiting vulnerabilities in the target websites or by infecting third-party services used by these sites. However, in this particular campaign, all victim websites were directly exploited. Malicious code snippets were surreptitiously inserted into the websites' first-party resources. The injected malicious code varied, at times being added to HTML pages, while in other instances, it was concealed within first-party scripts loaded as part of the website.
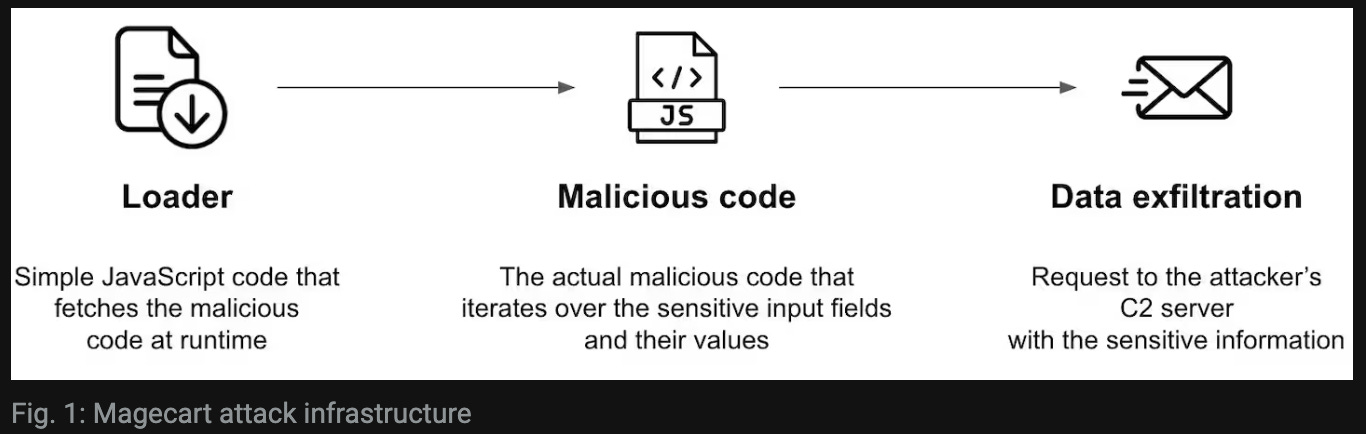
This campaign, like many other Magecart operations, consists of three key components: the loader, the malicious attack code, and data exfiltration. The loader is comprised of short, cryptic JavaScript code snippets responsible for loading the complete malicious attack code. The malicious attack code itself is the primary JavaScript component executing the attack, which identifies sensitive inputs, retrieves data, disrupts the checkout process, and injects counterfeit forms. Data exfiltration involves the method used to transmit stolen data to the attacker's command and control (C2) server.
The division of the attack into these three segments is intended to enhance concealment, making detection more challenging. This approach ensures that the full attack flow is only activated on specific targeted pages. Due to the obfuscation techniques employed by the attackers, full activation is limited to where they intend it to execute. Consequently, the attack becomes discreet and less prone to detection by security services and external scanning tools in place on the targeted websites.
While many Magecart campaigns follow a similar structure, what distinguishes one from another are the concealment techniques employed by the attackers. These techniques serve to obscure the attack's infrastructure, hide traces, complicate detection and reverse engineering efforts, and ultimately prolong the attack.
More details in “The Art of Concealment: A New Magecart Campaign That’s Abusing 404 Pages“
CyberAttack to Ukrainian Telecom Providers
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that threat actors conducted interference with a minimum of 11 telecommunications service providers within the country from May to September 2023. These intrusions, codenamed UAC-0165 by the agency, resulted in service disruptions for customers.
The attacks commenced with a reconnaissance phase, during which the perpetrators scanned the networks of telecom companies to identify exposed RDP or SSH interfaces and potential entry points. CERT-UA noted that the reconnaissance and exploitation activities were carried out from previously compromised servers, often located within the Ukrainian internet segment. To route traffic through these compromised nodes, the attackers employed Dante, SOCKS5, and other proxy servers.
What sets these attacks apart is the utilization of two specialized programs, POEMGATE and POSEIDON, designed for credential theft and remote control of infected hosts. Furthermore, a utility called WHITECAT was employed to erase any forensic evidence.
Another critical point of vulnerability lay in the persistence of unauthorized access to the provider's infrastructure. This was achieved through regular VPN accounts that lacked multi-factor authentication.
Once a successful breach was established, the attackers attempted to disable network and server equipment, with a particular focus on Mikrotik equipment and data storage systems.
In a related development, CERT-UA noted the occurrence of four phishing waves executed by a hacking group tracked as UAC-0006 during the first week of October 2023. The attackers used legitimate compromised email addresses to distribute SmokeLoader malware to PCs through various means. The primary aim of these attacks was to compromise the computers of accountants, with the intention of stealing authentication data and potentially altering financial documents in remote banking systems to facilitate unauthorized payments.
More details in “Features of destructive cyberattacks in relation to Ukrainian providers (CERT-UA#7627)“
Targeted a Critical 0-day Cisco Vulnerability
Attackers have leveraged a recently disclosed critical zero-day vulnerability (CVE-2023-20198) to compromise and infect numerous Cisco IOS XE devices with malicious implants. Threat intelligence firm VulnCheck reports that this vulnerability has been actively exploited in attacks aimed at Cisco IOS XE routers and switches featuring the Web User Interface (Web UI) with the HTTP or HTTPS Server feature enabled.
VulnCheck's scans of internet-facing Cisco IOS XE web interfaces have uncovered thousands of compromised and infected hosts. To assist in detecting these implants on affected devices, VulnCheck has released a scanner. The situation is severe, as exploiting the IOS XE vulnerability potentially grants attackers privileged access, enabling them to monitor network traffic, pivot into secure networks, and carry out man-in-the-middle attacks, according to VulnCheck CTO Jacob Baines.
While a patch is not yet available, organizations can protect themselves by disabling the web interface and removing all management interfaces from the internet. Cisco disclosed that unauthenticated attackers can exploit this zero-day vulnerability to attain full administrator privileges and gain complete remote control of affected Cisco routers and switches. Cisco has urged administrators to disable the vulnerable HTTP server feature on all internet-facing systems until a patch is released.
Cisco discovered these attacks in late September, following reports of unusual behavior on a customer device. Evidence of the attacks dates back to September 18, when the attackers created local user accounts named "cisco_tac_admin" and "cisco_support." The attackers also deployed malicious implants, which allowed them to execute arbitrary commands at the system or IOS levels on compromised devices.
Cisco believes that these clusters of activity likely originated from the same actor, with the October activity building on the September attacks. The company has recommended that administrators search for suspicious or recently created user accounts as potential signs of malicious activity related to this threat.
In September, Cisco issued a warning to customers to patch another zero-day vulnerability (CVE-2023-20109) in its IOS and IOS XE software that had also been targeted by attackers in the wild.
More details in “Cisco IOS XE Software Web UI Privilege Escalation Vulnerability“
Additional info in “Cisco warns of new IOS XE zero-day actively exploited in attacks“
Additional info in “VulnCheck - Widespread Cisco IOS XE Implants in the Wild“
XorDDoS Trojan targets Linux devices and systems
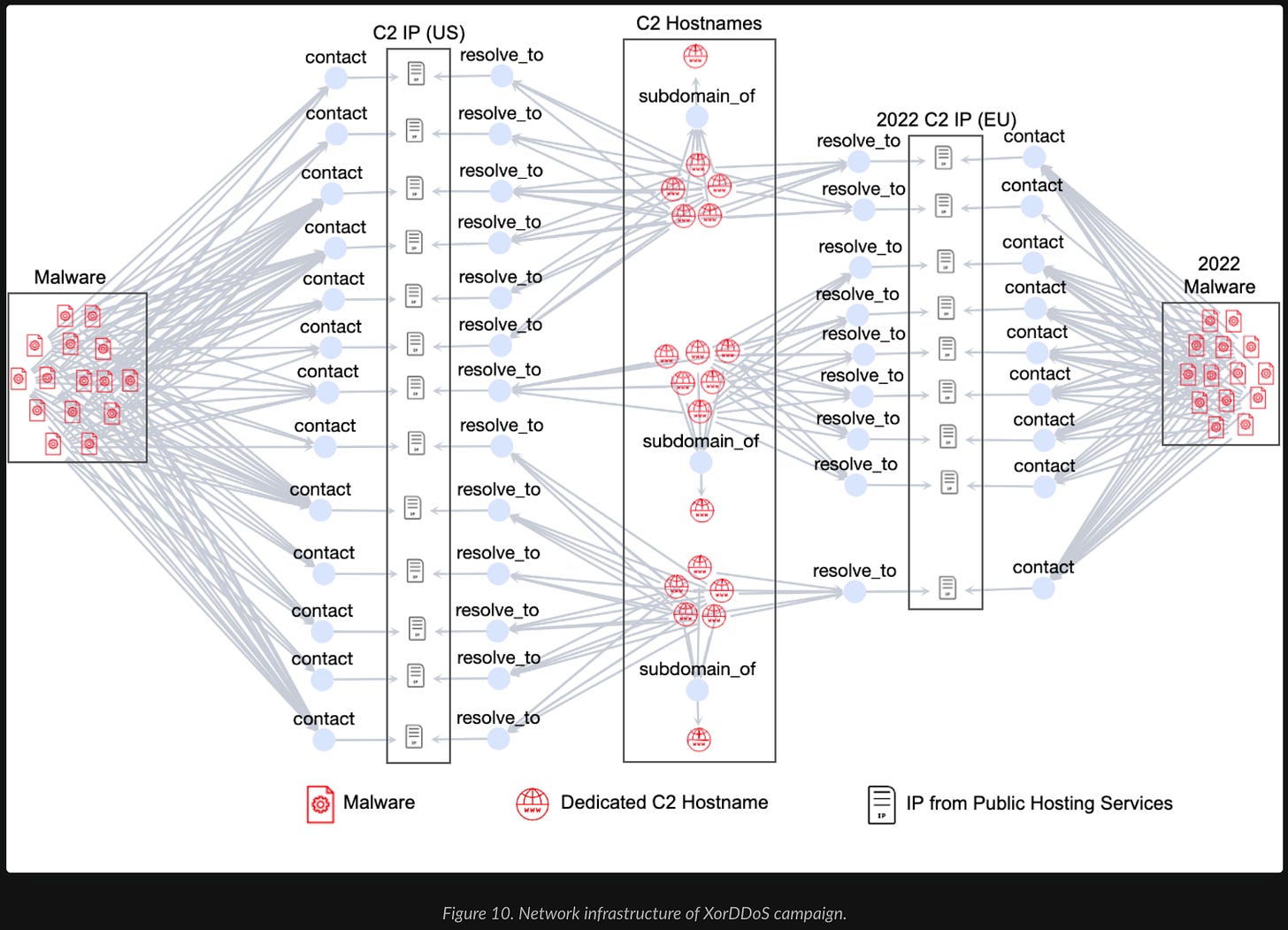
A new campaign has come to light involving the XorDDoS Trojan, which targets Linux systems and devices, effectively transforming them into remotely controllable zombies under the command of malicious actors. These compromised systems can subsequently be harnessed for Distributed Denial-of-Service (DDoS) attacks.
Comparing this latest campaign with one from 2022, the sole change observed pertains to the configuration of the C2 hosts, whereas the attacking domains remain consistent. Remarkably, the threat actors appear to have shifted their offensive infrastructure to hosts operating on legitimate public hosting services.
Despite many security vendors having classified the C2 domains as malicious and taking measures to block them, the current active malware traffic is being rerouted to new IP addresses.
The initial access vector employed by the threat actors involved scanning for hosts with HTTP services susceptible to directory traversal attacks, facilitating access to arbitrary files on the server. The attackers specifically targeted the /etc/passwd file to retrieve passwords, though they resorted to SSH brute-force attacks due to the file containing only encrypted passwords. Once access was gained, the threat actors downloaded malware from remote servers and assumed control of the system.
The XorDDoS Trojan employs an XOR encryption key (BB2FA36AAA9541F0) to encrypt execution-related data, which is subsequently decrypted using a decryption function. Once activated on the victim's machine, the malware retrieves crucial information such as /var/run/gcc.pid, OS version, malware version, memory status, and CPU information.
More details in “Blocking Dedicated Attacking Hosts Is Not Enough: In-Depth Analysis of a Worldwide Linux XorDDoS Campaign“
Additional info in “XorDDoS Infects Linux Devices And Uses Them To Carry Out DDoS Attacks“
Disrupting Human-Operated Attacks Automatically by Containing Compromised User Accounts
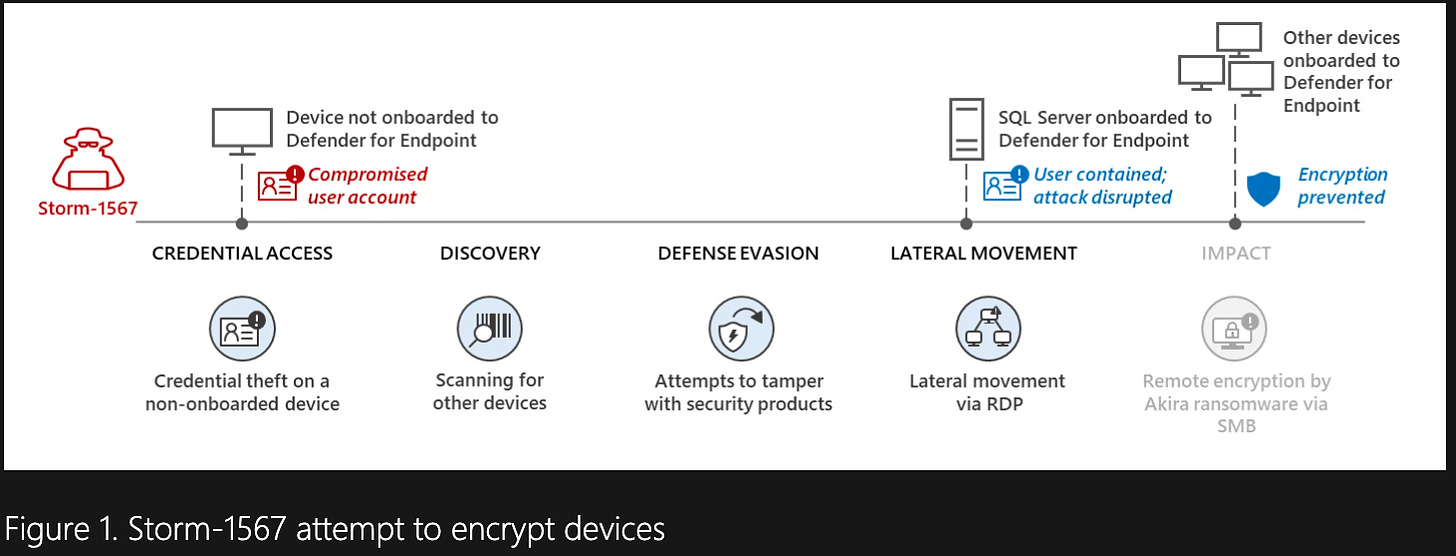
Attackers employ various methods, such as credential dumping, keylogging, and brute-forcing, to compromise user accounts. Weak credential management can swiftly lead to the breach of domain admin-level accounts, granting attackers access to domain resources and the entire network. Based on Microsoft's analysis, attackers can move from their initial access point to compromising domain admin-level accounts with just one hop. For example, an attacker might target an over-privileged service account on an outdated, vulnerable, internet-facing server.
Highly privileged user accounts are prime targets. Compromising domain admin-level accounts can bypass traditional security measures, including Active Directory. Attackers not only compromise existing accounts but also create additional dormant, highly privileged user accounts for persistence.
Microsoft Defender for Endpoint now includes user containment in its automatic attack disruption capability. User containment prevents compromised accounts from accessing network resources, even domain admin accounts. It activates when high-fidelity signals indicate a compromised user account in an ongoing attack.
The Microsoft blog discusses two real-world incidents where automatic attack disruption protected organizations by containing compromised user accounts. Microsoft's approach involves a multi-layer defense for optimal security protection across endpoints and identities. The automatic attack disruption's decentralized approach creates a security boundary to contain compromised user accounts, disrupting attacker activities like lateral movement and credential theft.
The capability incorporates multiple controls, including sign-in restrictions, intercepting SMB activity, filtering RPC activity, and disconnecting or terminating active sessions. User containment is part of Microsoft 365 Defender, and onboarding devices to Microsoft Defender for Endpoint enhances protection. This innovative solution is designed to defend against human-operated attacks, like ransomware, by correlating high-fidelity signals and automatically disrupting ongoing attacks.
More details in “Automatic disruption of human-operated attacks through containment of compromised user accounts“
Additional info in “Microsoft Defender for Endpoint now stops human-operated attacks on its own“
A.I. support for text drafting