[CyberLand News] Weekly #8 - Threats and Malware
Last news on threats, malware and vulnerabilties in the cyber land
Contents
Microsoft versus malicious Cobalt Strike infrastructure
Cryptomining attacks via Verblecon malware
PowerShell executed via WinRAR SFX to elude detection
Genesis Market seized
Cyberattack in a hybrid environment - Mercury threat actor
Rilide Crypto Stealer
Rorschach, a very fast ransomware
Telegram, the phishing kits
Microsoft versus malicious Cobalt Strike infrastructure
Microsoft, Fortra, and the Health Information Sharing and Analysis Center (Health-ISAC) have joined forces to combat cybercriminals using cracked copies of Cobalt Strike, a popular hacking tool. The makers of Cobalt Strike, Fortra, and Microsoft's Digital Crimes Unit (DCU) are determined to protect the legitimate use of security tools and products. The US District Court for the Eastern District of New York issued a court order allowing the two companies to seize domain names and take down IP addresses of servers hosting cracked versions of Cobalt Strike, with the help of relevant computer emergency readiness teams (CERTs) and internet service providers (ISPs).
The takedowns have already started, and the coalition is aiming to disrupt future malicious infrastructure used in attacks. Cobalt Strike was originally designed as a commercial penetration testing tool, but malicious actors obtained and distributed cracked copies, making it one of the most widely used tools in cyberattacks. Threat actors use it for post-exploitation tasks after deploying beacons designed to provide them with persistent remote access to compromised devices, leading to data theft and ransomware attacks.
Microsoft has detected malicious infrastructure hosting Cobalt Strike across the globe, and various state-backed threat actors and hacking groups have used cracked versions. The ransomware families linked to cracked copies of Cobalt Strike have cost hospital systems millions of dollars in recovery and repair costs and interruptions to critical patient care services.
Mode details in “Stopping cybercriminals from abusing security tools“
More details in “MITRE - Cobal Trike”
Additional info in “Making Cobalt Strike harder for threat actors to abuse“
Cryptomining attacks via Verblecon malware
Security researchers have issued a warning about a new malware loader, named Verblecon, which has been identified as being powerful enough to be used in ransomware and espionage attacks, although it is currently only being used for low-reward attacks. Verblecon is a Java-based malware that has a polymorphic nature, making it difficult to detect.
Symantec researchers discovered Verblecon in January 2022, being used to install cryptocurrency miners on compromised machines. The researchers also noted that the attacker may be interested in stealing access tokens for the Discord chat app. Verblecon is known to target non-enterprise machines, as they are rarely in the scope of more sophisticated threat actors because of their low profitability.
The researchers believe that Verblecon is currently being used by an actor who does not recognize the full damaging potential of this malware loader, but if more sophisticated cybercriminals gain access to it, they could use it for ransomware and espionage attacks. Symantec researchers have noted that while Verblecon is not currently being used for such attacks, its complex nature means it is capable of being used for more malicious purposes.
More details in “Verblecon: Sophisticated New Loader Used in Low-level Attacks“
PowerShell executed via WinRAR SFX to elude detection
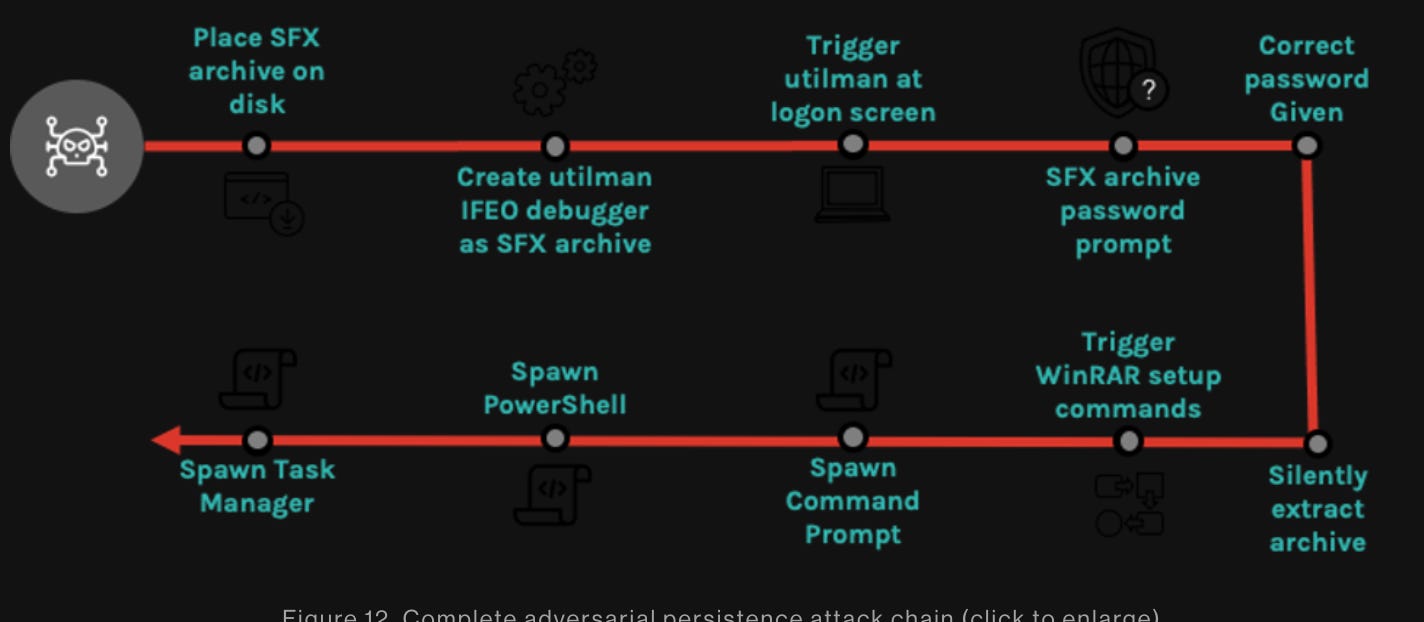
Hackers have found a new way to plant backdoors on target systems by adding malicious functionality to self-extracting archives (SFX) created using compression software such as WinRAR or 7-Zip.
These SFX archives contain harmless decoy files that allow the threat actor to avoid triggering security agents on the target system. The archives can be password-protected to prevent unauthorized access, and they simplify distribution of archived data to users who don't have an extraction utility.
Cybersecurity firm CrowdStrike recently discovered that an adversary had used stolen credentials to abuse the 'utilman.exe' application and launch a password-protected SFX file. The SFX file contained an empty text file that served as a decoy, while the real function was to abuse WinRAR's setup options and run PowerShell, Windows command prompt, and task manager with system privileges. Since the SFX archive could be run from the logon screen, the adversary had a persistent backdoor that could be accessed with the correct password. Traditional antivirus software is unlikely to detect this type of attack, so users are advised to use appropriate software to check the content of SFX archives and look for potential scripts or commands scheduled to run upon extraction.
More details in “How Falcon OverWatch Investigates Malicious Self-Extracting Archives, Decoy Files and Their Hidden Payloads“
Genesis Market seized
The FBI has seized the website of genesis.market, a notorious source of stolen credentials. Security firm Sophos identified genesis.market as an "invitation-only marketplace" that provided stolen credentials, cookies, and digital fingerprints obtained from compromised systems. Genesis.market was categorized as an initial access broker (IAB) that not only sold data but offered a subscription service to provide up-to-date information on individuals it tracked. The website offered customer-service features, including a polished interface with good data-correlation capabilities, an effective and well-maintained tool for customers, and mainstream accoutrements such as an FAQ, user support, pricing in dollars (though payment is in Bitcoin), and competent copyediting. The FBI acted with law enforcement agencies from around the world as Genesis Market used several domain names, making it difficult to take down. Sophos notes that the FBI's portrayal of its infosec operatives as faceless hoodie-wearers is a disincentive to legitimate infosec workers. Nonetheless, the world is safer after the seizure of genesis.market.
Additional info in “FBI obtained detailed database exposing 60,000 users of the cybercrime bazaar Genesis Market“
Additional info in “Genesis Market No Longer Feeds The Evil Cookie Monster“
Cyberattack in a hybrid environment - Mercury threat actor
According to a recent blog post from Microsoft Threat Intelligence, MERCURY, a nation-state actor believed to be connected to the Iranian government, has carried out destructive attacks on both on-premises and cloud environments. While the attackers attempted to disguise their activities as a ransomware campaign, the ultimate goal of the operation was destruction and disruption.
Previous MERCURY attacks have targeted on-premises environments, but this time the impact extended to destruction of cloud resources. Microsoft believes that MERCURY likely collaborated with another actor, known as DEV-1084, who carried out the destructive actions after MERCURY gained access to the target environment.
MERCURY probably took advantage of known vulnerabilities in unpatched applications for initial access before handing off access to DEV-1084, who then carried out extensive reconnaissance and discovery, established persistence, and moved laterally throughout the network.
DEV-1084 was then observed using highly privileged credentials to destroy resources such as server farms, virtual machines, and storage accounts, as well as sending emails to internal and external recipients.
The blog post provides detailed analysis of the actor activity and related tools, and offers guidance to the community and industry partners on how to detect these attacks. Microsoft has also directly notified targeted or compromised customers, providing them with important information to secure their environments.
More details in “MERCURY and DEV-1084: Destructive attack on hybrid environment“
Rilide Crypto Stealer
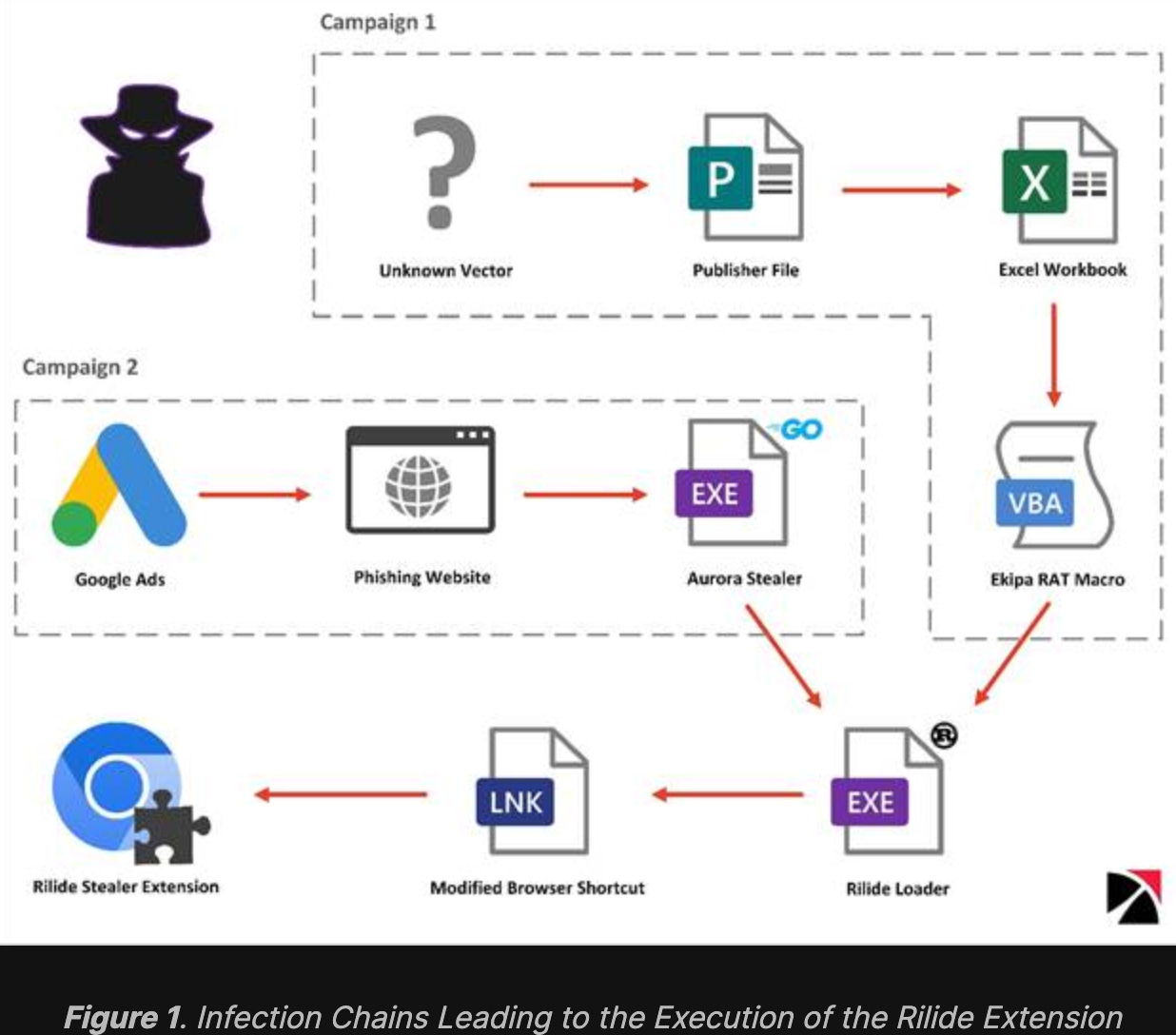
The Trustwave SpiderLabs cybersecurity researchers have discovered a new strain of Rilide malware that targets Chromium-based browsers, such as Google Chrome, Microsoft Edge, and Opera, to steal cryptocurrency funds and monitor users' browsing activities.
The malware is unique because it can generate dialogues to trick users into giving away their 2FA keys, allowing the attacker to withdraw cryptocurrencies discreetly. Additionally, the malware can capture screenshots, monitor browsing history, and inject malicious scripts to steal funds from cryptocurrency wallets. The researchers have confirmed that the malware is hidden in a legitimate-looking Google Drive extension.
During their investigation, SpiderLabs detected multiple such extensions for sale in March 2022. The C2 address embedded in the Rilide code can identify GitHub repositories belonging to a user named gulantin, which contains the extension's loader.
More details in “Rilide: A New Malicious Browser Extension for Stealing Cryptocurrencies“
Rorschach, a very fast ransomware
Check Point Research and Check Point Incident Response Team have uncovered a new ransomware strain named Rorschach that was used in an attack against a US-based company.
Rorschach ransomware is one of the fastest ransomware strains detected so far. In a controlled environment, the researchers conducted five separate encryption speed tests, limited to local drive encryption only, and found that Rorschach was able to encrypt files in just four minutes and 30 seconds. The ransomware is highly customizable and uses direct syscalls, and it uses DLL side-loading of a Cortex XDR Dump Service Tool to deploy. The ransomware also contains unique functions, such as spawning processes in suspend mode to give falsified arguments to harden analysis and remediation efforts, supports a self-propagating process, and supports effective binary and anti-analysis protection techniques and evasive mechanisms. The researchers also found hidden and obfuscated built-in options that can be used by operators to remotely control the ransomware. The ransomware does not infect systems used in the CIS countries.
More details in “Rorschach - A new sophisticated and fast ransomware“
Telegram, the phishing kits
According to a report by Kaspersky, cybercriminals are increasingly using the messaging platform Telegram to peddle phishing kits and set up phishing campaigns. These phishers create Telegram channels to educate their audience about phishing and share polls, which are then distributed via YouTube, GitHub, and the phishing kits developed by the crooks themselves.
The Russian cybersecurity firm detected over 2.5 million malicious URLs generated using phishing kits in the past six months. One of the services offered is to provide threat actors with Telegram bots that automate the process of generating phishing pages and collecting user data. In some cases, phishers share users' personal data with other subscribers for free to attract aspiring criminals, only to sell paid kits to those who wish to pull off more such attacks. Paid services include advanced kits with features like anti-bot detection, URL encryption, and geoblocking.
Phishing services are marketed via Telegram on a subscription basis, and a one-time password (OTP) bot that calls users and convinces them to enter the two-factor authentication code on their phones to help bypass account protections is also promoted as a subscription.
These findings follow an advisory from Cofense earlier this year, which revealed an 800% increase year-over-year in the use of Telegram bots as exfiltration destinations for phished information.
More details in “The Telegram phishing market“
Additional info in “Abuse of Telegram Bots Rises 800% in 2022“
A.I. support for text and images