Intro
The Lazarus Group is a cybercrime group with ties to the North Korean government, consisting of an unknown number of individuals. Researchers have linked the group to various cyberattacks from 2010 to 2023, leading to their designation as an Advanced Persistent Threat (APT) due to their intended nature, threat level, and wide range of methods.
Different cybersecurity organizations refer to them by different names, such as Hidden Cobra and Zinc. The United States FBI considers them a North Korean state-sponsored hacking organization, and defectors have referred to them as the 414 Liaison Office. North Korea benefits from these cyber operations because they can create an asymmetric threat using a small group of operators, particularly against South Korea.
The Lazarus Group is composed of at least two subgroups, both known as Andariel and BlueNoroff, and has notable overlaps with the adversaries known as APT37 and Kimsuky.
The group was involved in a cyber-espionage campaign called "Operation Troy" that used unsophisticated distributed denial-of-service (DDoS) techniques against the South Korean government. Over time, their techniques became more advanced, as demonstrated by their 2014 attack on Sony Pictures. The group has also targeted banks in Ecuador, Vietnam, Poland, and Mexico, and was responsible for the 2016 Bangladesh Bank heist. The group's origins are unclear, but it is widely believed to be linked to North Korea. Some cybersecurity firms have attributed specific sub-groups within Lazarus, such as Bluenoroff, to certain types of attacks. However, some experts have suggested that Lazarus may use "false flag" techniques to mislead investigators and pin attacks on other countries, as seen with the WannaCry attack.
Lazarus Attacks & Operations
Below a timeline concerning the main attack and operations linked to Lazarus group:
2008 – Operation Flame
2009 – Operation Troy
2011 – 10 Days of Rain
2012 – Operation 1Mission
2013 – Operation Dark Seoul
2014 – Sony Breach
2016 – Bangladesh Bank Heist
2017 – WannaCry Ransomware Attack
2020 – Pharmaceutical Company Attacks
2022 – American Energy Firms Attacks
2022 – Axie Infinity attack
2022 – Massive Spear Phishing Attacks
2022 – Crypto Stealer Malware Attack
2022 – Harmony Hack
2022 – Attacks to Healthcare research organizations
For details and additional info, see the resources shared at the end of the article.
Lazarus Targets
The Lazarus Group's primary objectives are to engage in espionage, steal data, carry out disruptive attacks, and gain financial profits that support state goals, which may include political and national security objectives, military research and development, and evading international sanctions.
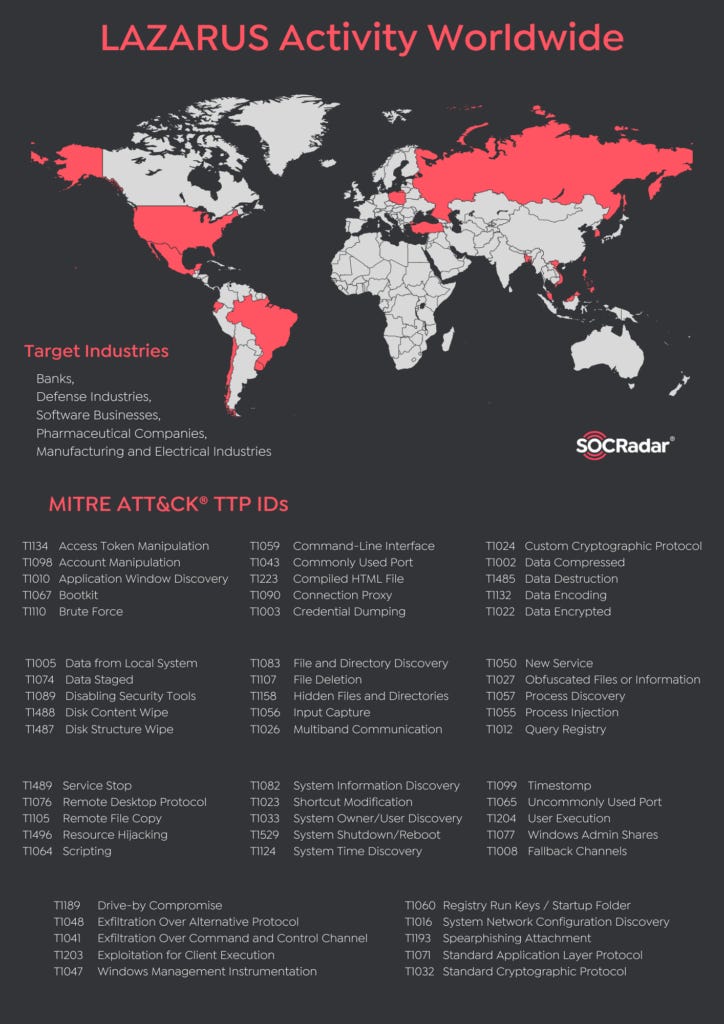
The Lazarus Group primarily focuses on a wide range of targets around the world, including but not limited to government organizations, defense institutions, financial institutions, media outlets, and critical infrastructure entities.
During the 2022, the APT has been found to target a number of countries, with the United States and Japan being the most commonly attacked, with 9 and 8 campaigns respectively. Other countries of interest to the group include Singapore, India, and the United Kingdom, as evidenced by their participation in multiple campaigns. While Lazarus Group typically targets entities for financial gain, they may choose to attack multiple targets for high returns, similar to other financially motivated cyber criminals. However, some of their recent campaigns have targeted only specific countries, with Japan being the sole target of campaigns such as MUD NATIONALS, UNC029, and UNC028, while other countries were targeted in just one campaign. Focusing on the target typology, the Lazarus Group launched cyberattacks against organizations in over 20 different industries. The group primarily targeted industrial conglomerates, with a focus on those in the financial, IT, and automotive sectors.
Looking the entire Lazarus story:
Targeted Countries: Bangladesh, Brazil, Canada, Chile, China, France, Germany, Hong Kong, India, Indonesia, Iran, Japan, Myanmar, Philippines, Poland, South Korea, Russia, Thailand, UK, USA, Vietnam
Targeted Industries: Aerospace & Defense, Banks & Capital Markets, Cryptocurrency, Energy, Entertainment/Gaming, Media, Real Estate, IT & Telecommunications,
Lazarus TTP and Tools
The Lazarus group has been observed using a range of tactics and tools in their operations, such as Distributed Denial of Service (DDoS) attacks, wiping data from systems, and misdirection techniques like disguising their attacks as hacktivist activity or staging a "false flag" scenario. They also use spear-phishing, supply-chain attacks, watering hole attacks that exploit vulnerabilities in Active-X, and vulnerabilities in security and IT asset management systems. The malware associated with the group includes a number of tools such as DarkComet RAT, Mimikatz, Net, Nestegg, AppleJeus, Macktruck, WannaCry, WhiteOut, Quickcafe, Rawhide, Smotthride, TightVNC, Sorrybrute, Keylime, Cryptoistic, Snapshot, Mapmaker, net.exe, sysmon, Bootwreck, Cleantoad, Closeshave, Dyepack, the Hermes ransomware, TwoPence, Electricfish, PowerRatankba, PowerSpritz, RawDisk, netsh, Proxysvc, Dtrack, and others.
The group employs a range of techniques in their cyber operations, including phishing, brute-force attacks, backdoors, drive-by compromise, watering hole attacks, exploitation of vulnerabilities in insecure old versions of Apache Struts 2, as well as hacking into Linux servers.
Having a high level overview on the TTPs, there are:
Reconnaissance for fine tuned Spear Phishing
Destructive and Advanced Malware
Legitimate tools during the breach activities
Compromised legitimate servers for C2
IP Addresses for C2 over Domain names
Proxies in the C2 communication path
P2P communication with C2
Image ©SOCRadar - Article
External Resources & References
Lazarus APT leverages Windows Update client, GitHub in latest campaign
North Korea Targeted South Korean Cryptocurrency Users and Exchange in Late 2017 Campaign
North Korean State-Sponsored Lazarus Group Targets North American Energy Firms
North Korean Lazarus APT group targets blockchain tech companies
AttackIQ - Emulating the Highly Sophisticated North Korean Adversary Lazarus Group
AttackIQ - Emulating the Politically Motivated North Korean Adversary Andariel
AttackIQ - Emulating the Financially Motivated North Korean Adversary BlueNoroff
A.I. support for text and images